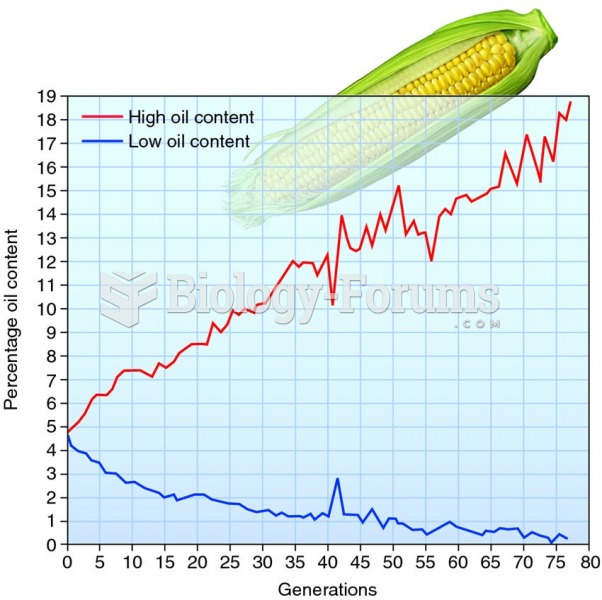
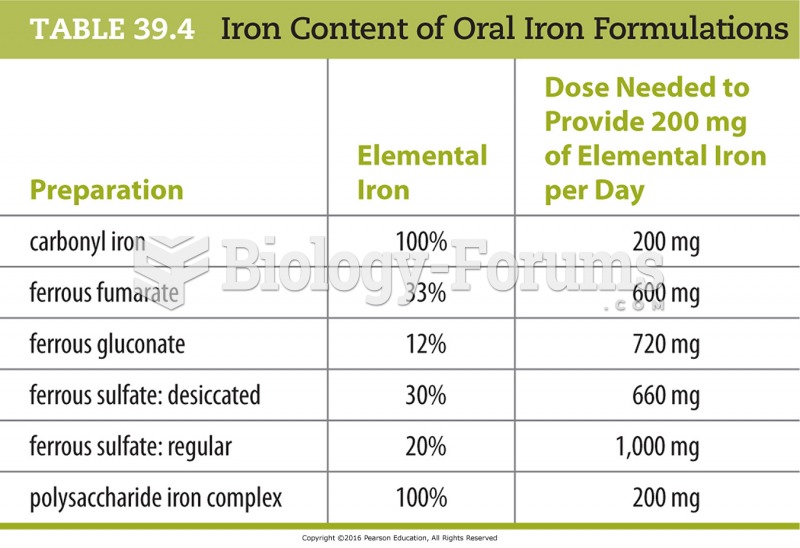
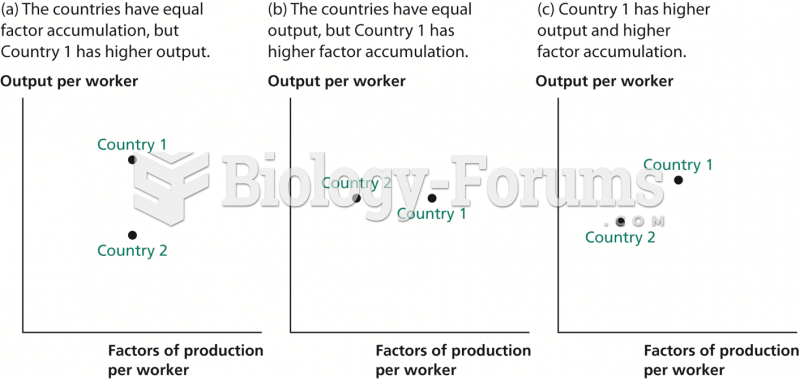
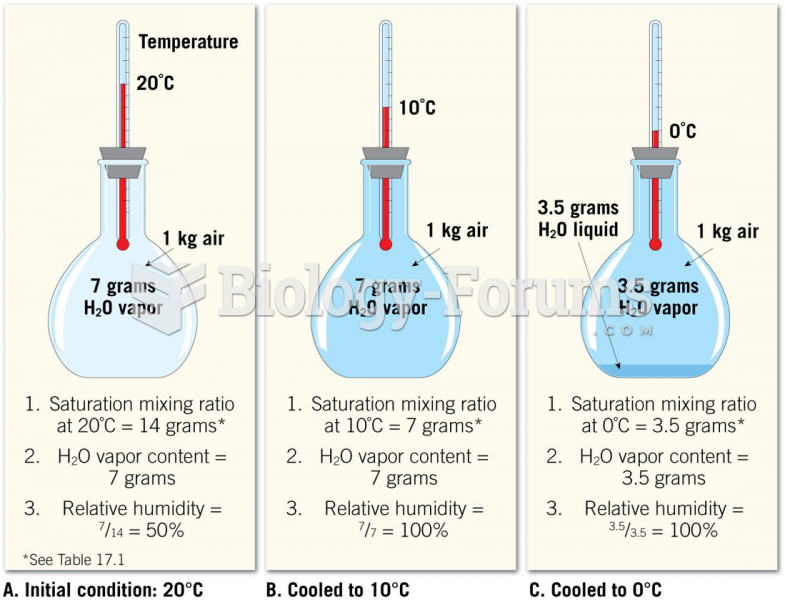
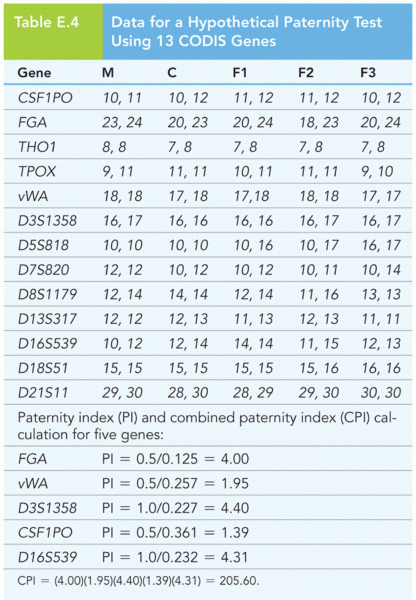
|
|
|
The strongest synthetic topical retinoid drug available, tazarotene, is used to treat sun-damaged skin, acne, and psoriasis.
The Babylonians wrote numbers in a system that used 60 as the base value rather than the number 10. They did not have a symbol for "zero."
HIV testing reach is still limited. An estimated 40% of people with HIV (more than 14 million) remain undiagnosed and do not know their infection status.
In 1835 it was discovered that a disease of silkworms known as muscardine could be transferred from one silkworm to another, and was caused by a fungus.
Despite claims by manufacturers, the supplement known as Ginkgo biloba was shown in a study of more than 3,000 participants to be ineffective in reducing development of dementia and Alzheimer’s disease in older people.