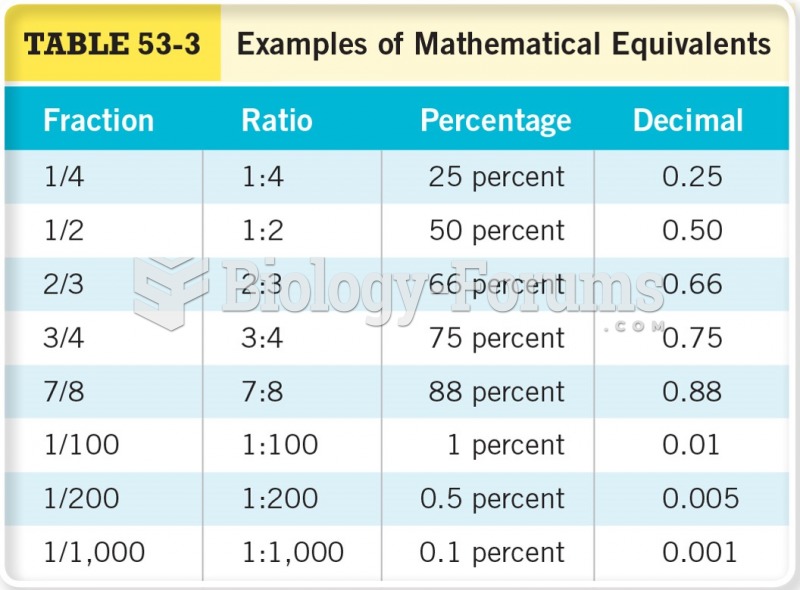
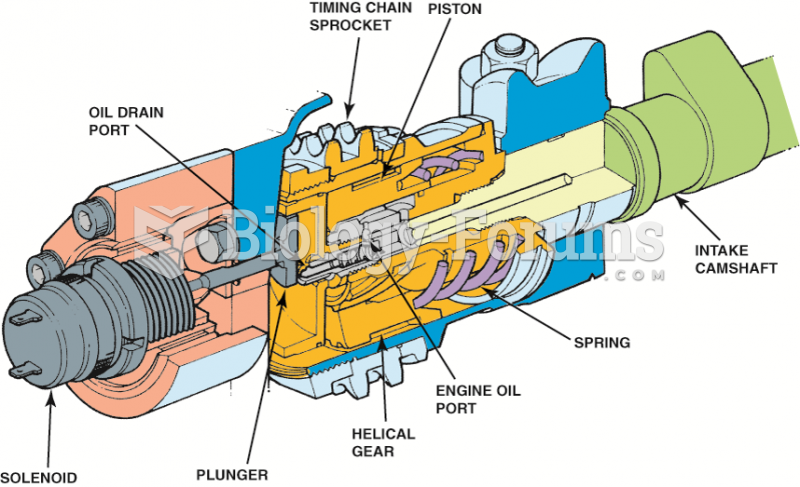
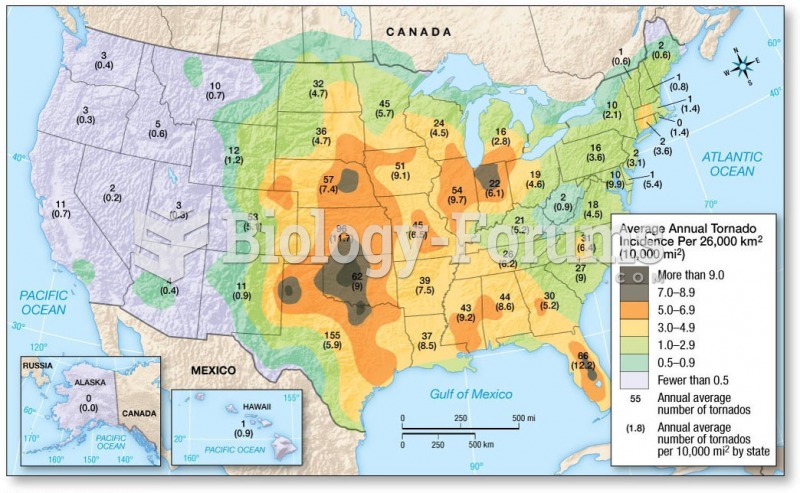
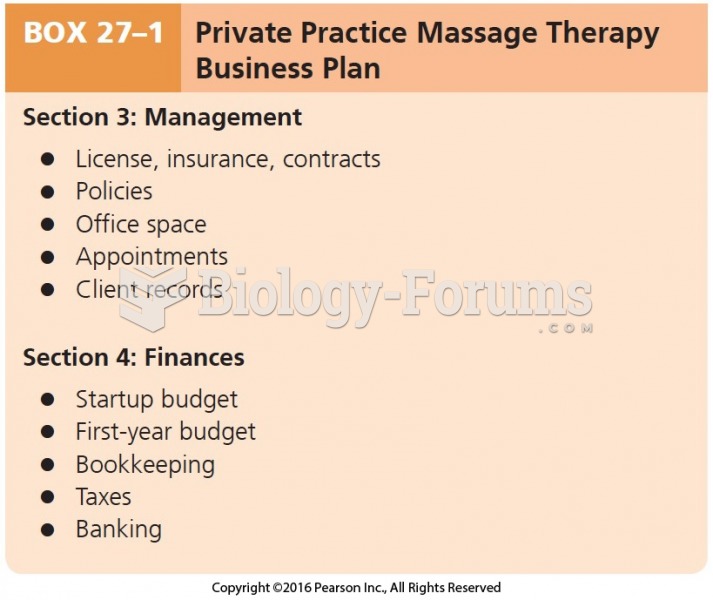
|
|
|
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.
The eye muscles are the most active muscles in the whole body. The external muscles that move the eyes are the strongest muscles in the human body for the job they have to do. They are 100 times more powerful than they need to be.
Human neurons are so small that they require a microscope in order to be seen. However, some neurons can be up to 3 feet long, such as those that extend from the spinal cord to the toes.
Alzheimer's disease affects only about 10% of people older than 65 years of age. Most forms of decreased mental function and dementia are caused by disuse (letting the mind get lazy).
The first-known contraceptive was crocodile dung, used in Egypt in 2000 BC. Condoms were also reportedly used, made of animal bladders or intestines.