|
|
|
Certain rare plants containing cyanide include apricot pits and a type of potato called cassava. Fortunately, only chronic or massive ingestion of any of these plants can lead to serious poisoning.
The first monoclonal antibodies were made exclusively from mouse cells. Some are now fully human, which means they are likely to be safer and may be more effective than older monoclonal antibodies.
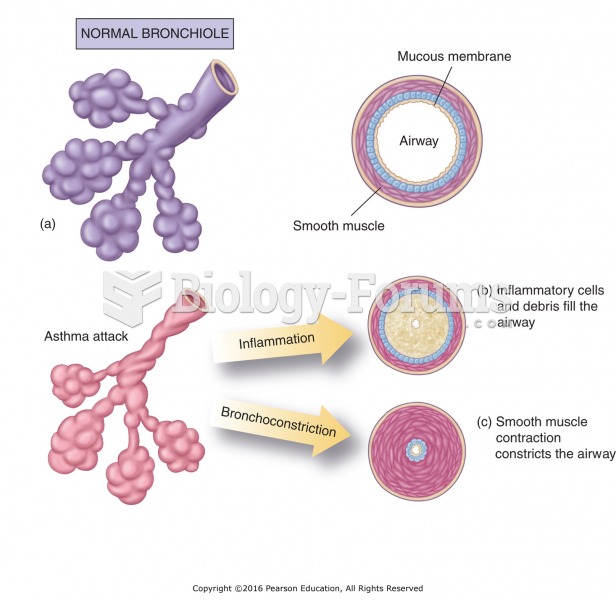
Acute bronchitis is an inflammation of the breathing tubes (bronchi), which causes increased mucus production and other changes. It is usually caused by bacteria or viruses, can be serious in people who have pulmonary or cardiac diseases, and can lead to pneumonia.
Most fungi that pathogenically affect humans live in soil. If a person is not healthy, has an open wound, or is immunocompromised, a fungal infection can be very aggressive.
Children with strabismus (crossed eyes) can be treated. They are not able to outgrow this condition on their own, but with help, it can be more easily corrected at a younger age. It is important for infants to have eye examinations as early as possible in their development and then another at age 2 years.
 SpaceShipOne completed the first manned private spaceflight in 2004, reaching an altitude of 100.124
SpaceShipOne completed the first manned private spaceflight in 2004, reaching an altitude of 100.124
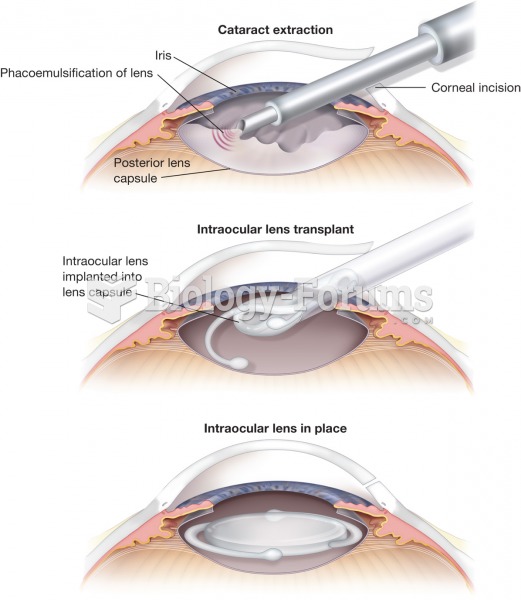 Cataract extraction. The procedure involves a surgical removal of a cataract lens and its replacemen
Cataract extraction. The procedure involves a surgical removal of a cataract lens and its replacemen