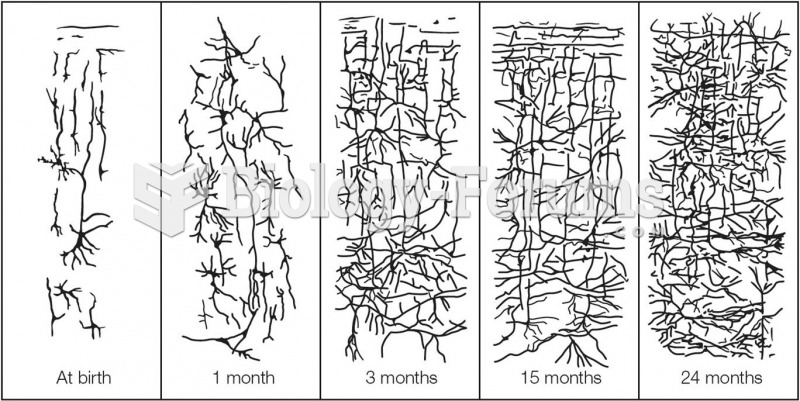
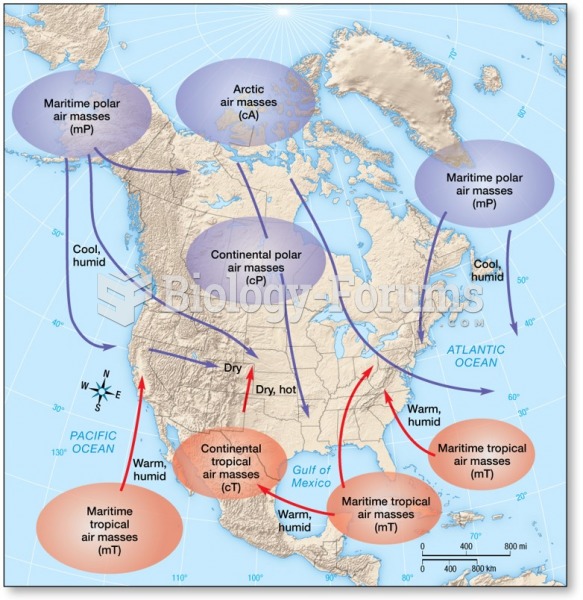
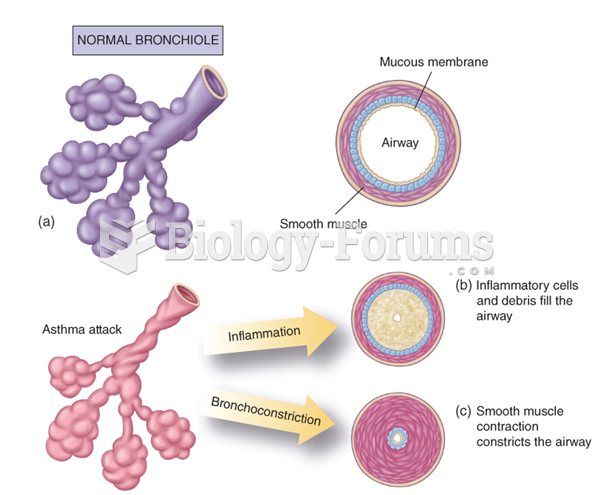
|
|
|
Complications of influenza include: bacterial pneumonia, ear and sinus infections, dehydration, and worsening of chronic conditions such as asthma, congestive heart failure, or diabetes.
Human stomach acid is strong enough to dissolve small pieces of metal such as razor blades or staples.
Human kidneys will clean about 1 million gallons of blood in an average lifetime.
Vampire bats have a natural anticoagulant in their saliva that permits continuous bleeding after they painlessly open a wound with their incisors. This capillary blood does not cause any significant blood loss to their victims.
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.