|
|
|
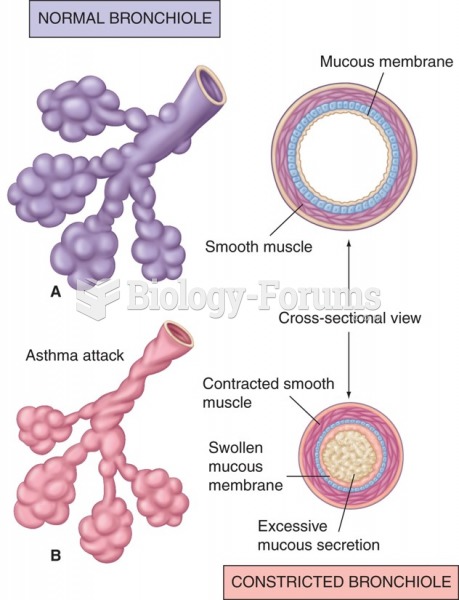
According to the National Institute of Environmental Health Sciences, lung disease is the third leading killer in the United States, responsible for one in seven deaths. It is the leading cause of death among infants under the age of one year.
The first oncogene was discovered in 1970 and was termed SRC (pronounced "SARK").
In 2006, a generic antinausea drug named ondansetron was approved. It is used to stop nausea and vomiting associated with surgery, chemotherapy, and radiation therapy.
The largest baby ever born weighed more than 23 pounds but died just 11 hours after his birth in 1879. The largest surviving baby was born in October 2009 in Sumatra, Indonesia, and weighed an astounding 19.2 pounds at birth.
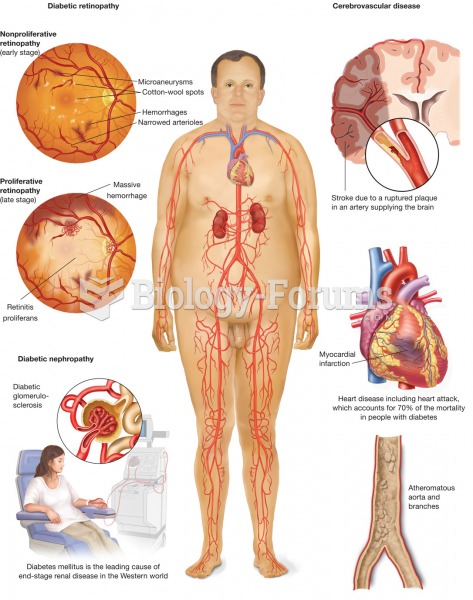
Serum cholesterol testing in adults is recommended every 1 to 5 years. People with diabetes and a family history of high cholesterol should be tested even more frequently.