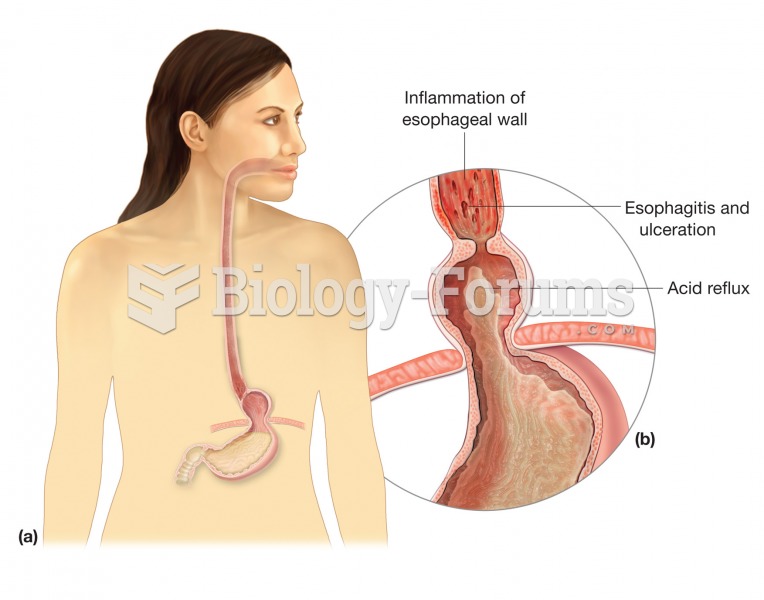
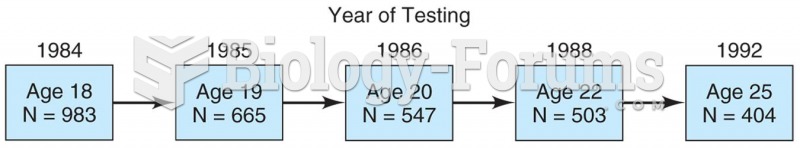
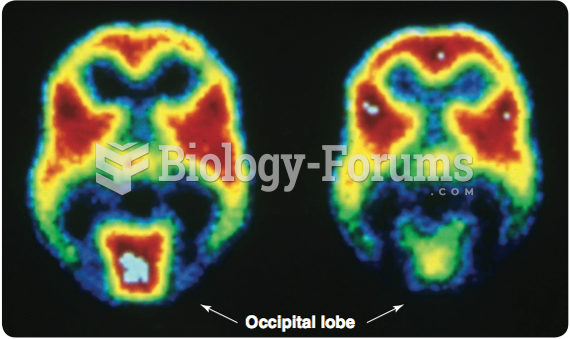
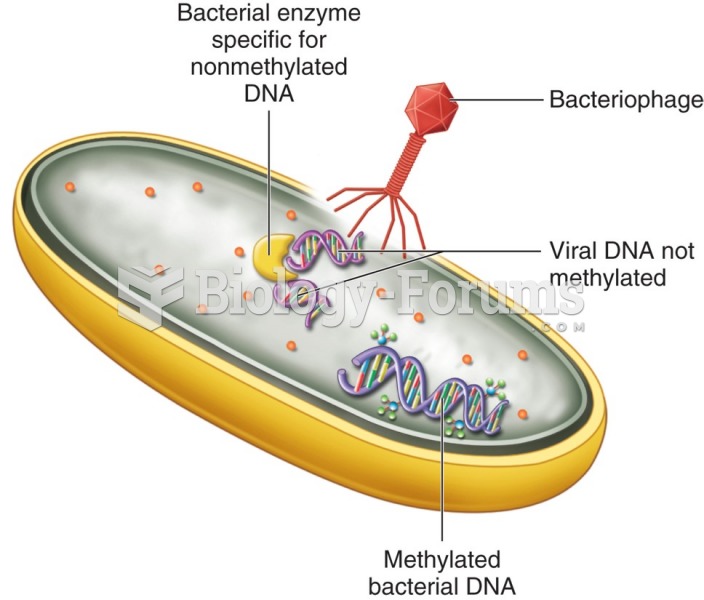
|
|
|
There are immediate benefits of chiropractic adjustments that are visible via magnetic resonance imaging (MRI). It shows that spinal manipulation therapy is effective in decreasing pain and increasing the gaps between the vertebrae, reducing pressure that leads to pain.
Interferon was scarce and expensive until 1980, when the interferon gene was inserted into bacteria using recombinant DNA technology, allowing for mass cultivation and purification from bacterial cultures.
Acute bronchitis is an inflammation of the breathing tubes (bronchi), which causes increased mucus production and other changes. It is usually caused by bacteria or viruses, can be serious in people who have pulmonary or cardiac diseases, and can lead to pneumonia.
Adults are resistant to the bacterium that causes Botulism. These bacteria thrive in honey – therefore, honey should never be given to infants since their immune systems are not yet resistant.
Calcitonin is a naturally occurring hormone. In women who are at least 5 years beyond menopause, it slows bone loss and increases spinal bone density.