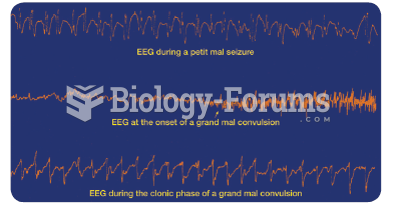
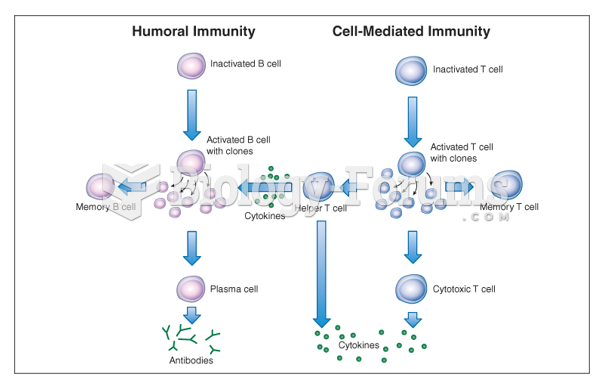
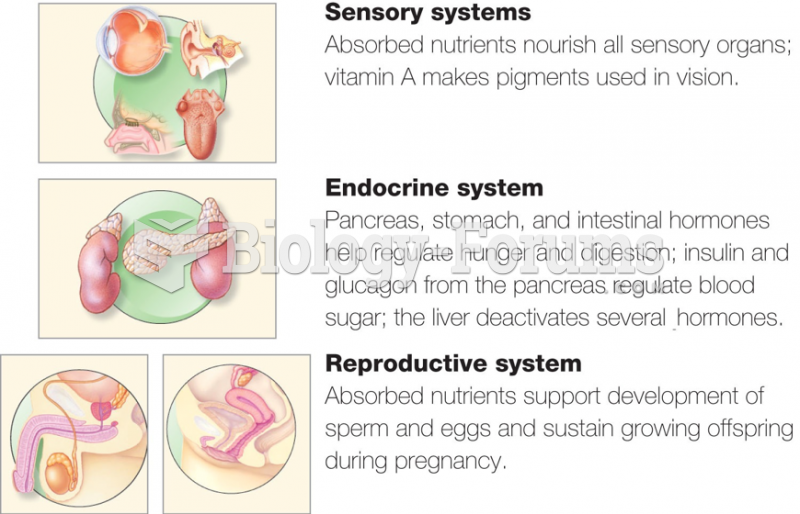
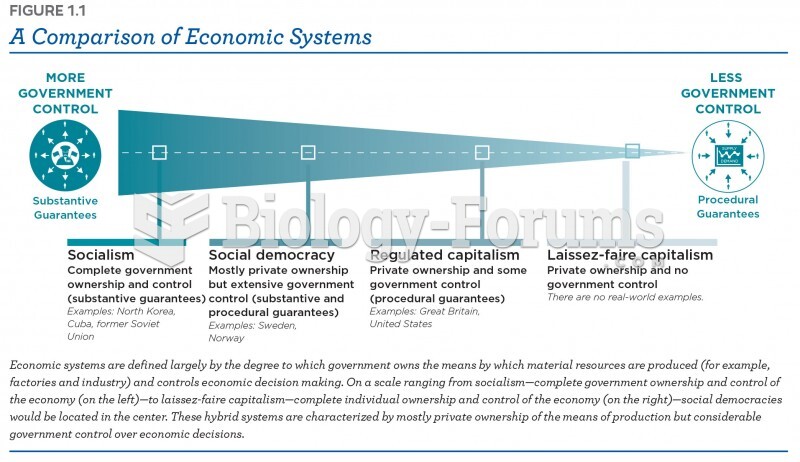
|
|
|
About one in five American adults and teenagers have had a genital herpes infection—and most of them don't know it. People with genital herpes have at least twice the risk of becoming infected with HIV if exposed to it than those people who do not have genital herpes.
The use of salicylates dates back 2,500 years to Hippocrates's recommendation of willow bark (from which a salicylate is derived) as an aid to the pains of childbirth. However, overdosage of salicylates can harm body fluids, electrolytes, the CNS, the GI tract, the ears, the lungs, the blood, the liver, and the kidneys and cause coma or death.
Your skin wrinkles if you stay in the bathtub a long time because the outermost layer of skin (which consists of dead keratin) swells when it absorbs water. It is tightly attached to the skin below it, so it compensates for the increased area by wrinkling. This happens to the hands and feet because they have the thickest layer of dead keratin cells.
Increased intake of vitamin D has been shown to reduce fractures up to 25% in older people.
Ether was used widely for surgeries but became less popular because of its flammability and its tendency to cause vomiting. In England, it was quickly replaced by chloroform, but this agent caused many deaths and lost popularity.