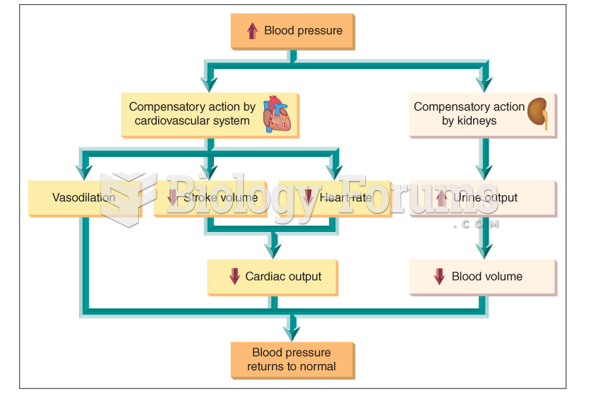
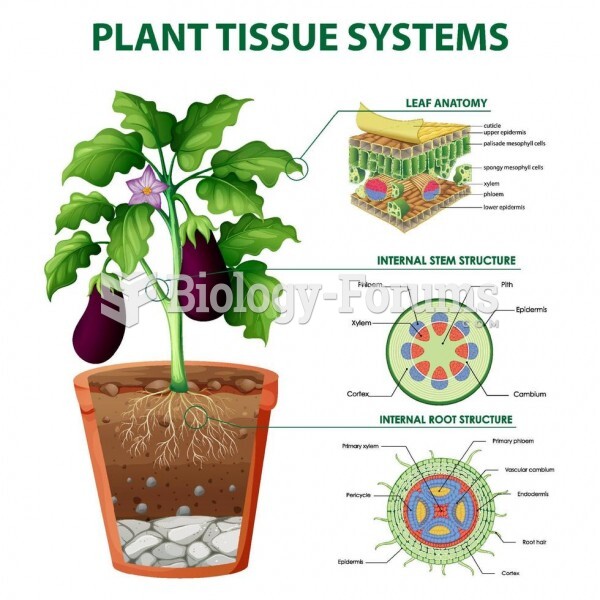
|
|
|
Not getting enough sleep can greatly weaken the immune system. Lack of sleep makes you more likely to catch a cold, or more difficult to fight off an infection.
Looking at the sun may not only cause headache and distort your vision temporarily, but it can also cause permanent eye damage. Any exposure to sunlight adds to the cumulative effects of ultraviolet (UV) radiation on your eyes. UV exposure has been linked to eye disorders such as macular degeneration, solar retinitis, and corneal dystrophies.
The use of salicylates dates back 2,500 years to Hippocrates's recommendation of willow bark (from which a salicylate is derived) as an aid to the pains of childbirth. However, overdosage of salicylates can harm body fluids, electrolytes, the CNS, the GI tract, the ears, the lungs, the blood, the liver, and the kidneys and cause coma or death.
Street names for barbiturates include reds, red devils, yellow jackets, blue heavens, Christmas trees, and rainbows. They are commonly referred to as downers.
Adolescents often feel clumsy during puberty because during this time of development, their hands and feet grow faster than their arms and legs do. The body is therefore out of proportion. One out of five adolescents actually experiences growing pains during this period.