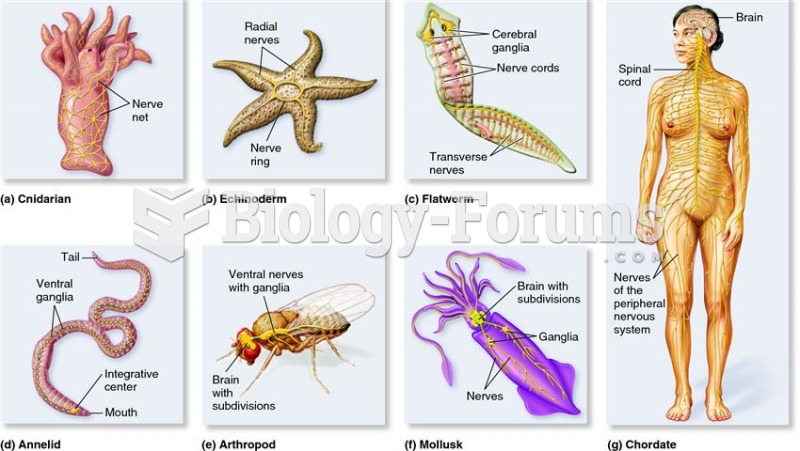
|
|
|
Certain rare plants containing cyanide include apricot pits and a type of potato called cassava. Fortunately, only chronic or massive ingestion of any of these plants can lead to serious poisoning.
According to the FDA, adverse drug events harmed or killed approximately 1,200,000 people in the United States in the year 2015.
In the ancient and medieval periods, dysentery killed about ? of all babies before they reach 12 months of age. The disease was transferred through contaminated drinking water, because there was no way to adequately dispose of sewage, which contaminated the water.
Once thought to have neurofibromatosis, Joseph Merrick (also known as "the elephant man") is now, in retrospect, thought by clinical experts to have had Proteus syndrome. This endocrine disease causes continued and abnormal growth of the bones, muscles, skin, and so on and can become completely debilitating with severe deformities occurring anywhere on the body.
Elderly adults are at greatest risk of stroke and myocardial infarction and have the most to gain from prophylaxis. Patients ages 60 to 80 years with blood pressures above 160/90 mm Hg should benefit from antihypertensive treatment.