|
|
|
Pregnant women usually experience a heightened sense of smell beginning late in the first trimester. Some experts call this the body's way of protecting a pregnant woman from foods that are unsafe for the fetus.
Most strokes are caused when blood clots move to a blood vessel in the brain and block blood flow to that area. Thrombolytic therapy can be used to dissolve the clot quickly. If given within 3 hours of the first stroke symptoms, this therapy can help limit stroke damage and disability.
Vaccines prevent between 2.5 and 4 million deaths every year.
Addicts to opiates often avoid treatment because they are afraid of withdrawal. Though unpleasant, with proper management, withdrawal is rarely fatal and passes relatively quickly.
Studies show that systolic blood pressure can be significantly lowered by taking statins. In fact, the higher the patient's baseline blood pressure, the greater the effect of statins on his or her blood pressure.
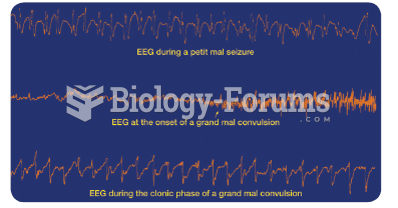 Cortical EEG recorded during epileptic attacks. Notice that each trace is characterized by epileptic ...
Cortical EEG recorded during epileptic attacks. Notice that each trace is characterized by epileptic ...
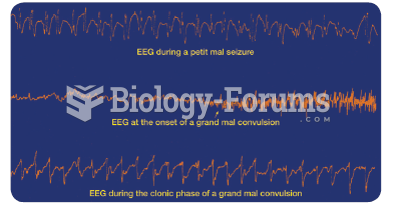 Cortical EEG recorded during epileptic attacks. Notice that each trace is characterized by epileptic ...
Cortical EEG recorded during epileptic attacks. Notice that each trace is characterized by epileptic ...