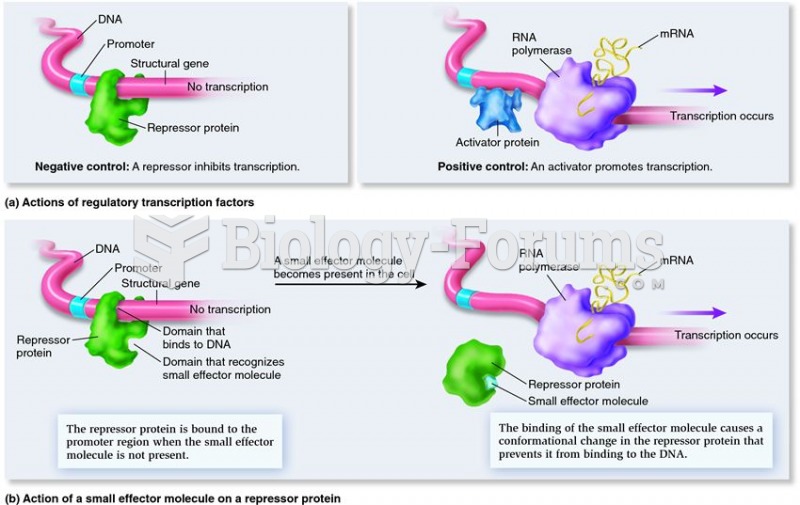
|
|
|
Historic treatments for rheumatoid arthritis have included gold salts, acupuncture, a diet consisting of apples or rhubarb, nutmeg, nettles, bee venom, bracelets made of copper, prayer, rest, tooth extractions, fasting, honey, vitamins, insulin, snow collected on Christmas, magnets, and electric convulsion therapy.
Pink eye is a term that refers to conjunctivitis, which is inflammation of the thin, clear membrane (conjunctiva) over the white part of the eye (sclera). It may be triggered by a virus, bacteria, or foreign body in the eye. Antibiotic eye drops alleviate bacterial conjunctivitis, and antihistamine allergy pills or eye drops help control allergic conjunctivitis symptoms.
For pediatric patients, intravenous fluids are the most commonly cited products involved in medication errors that are reported to the USP.
Amoebae are the simplest type of protozoans, and are characterized by a feeding and dividing trophozoite stage that moves by temporary extensions called pseudopodia or false feet.
Drugs are in development that may cure asthma and hay fever once and for all. They target leukotrienes, which are known to cause tightening of the air passages in the lungs and increase mucus productions in nasal passages.