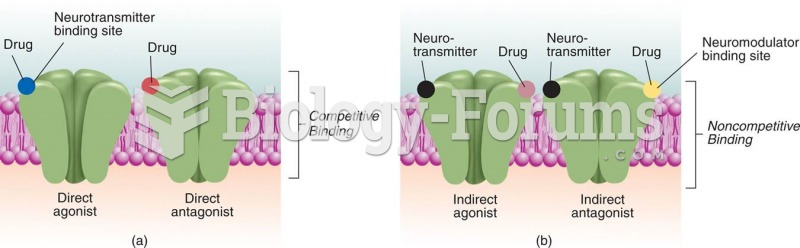
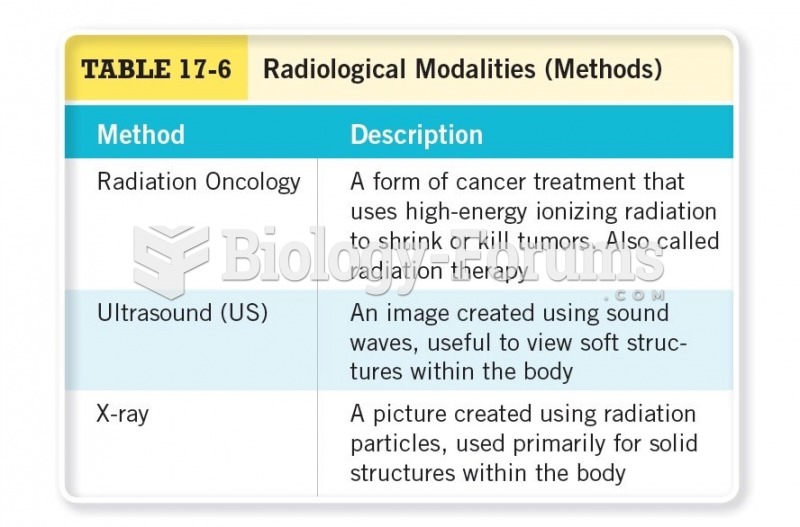
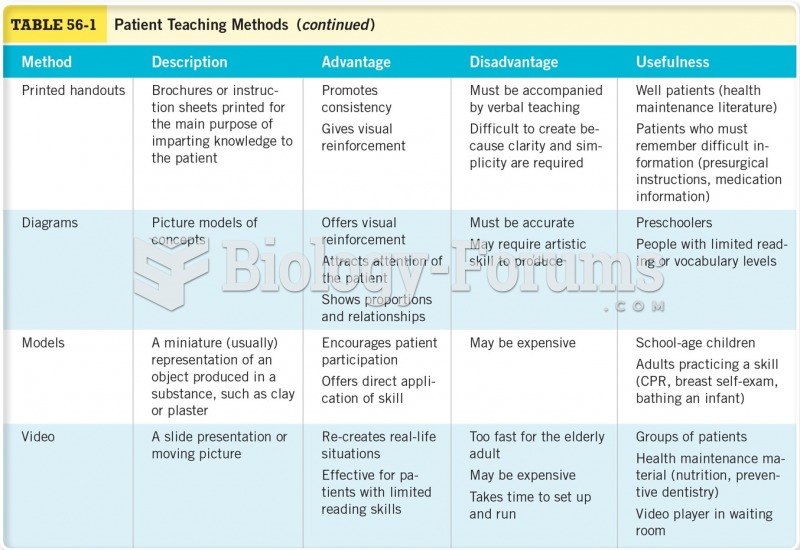
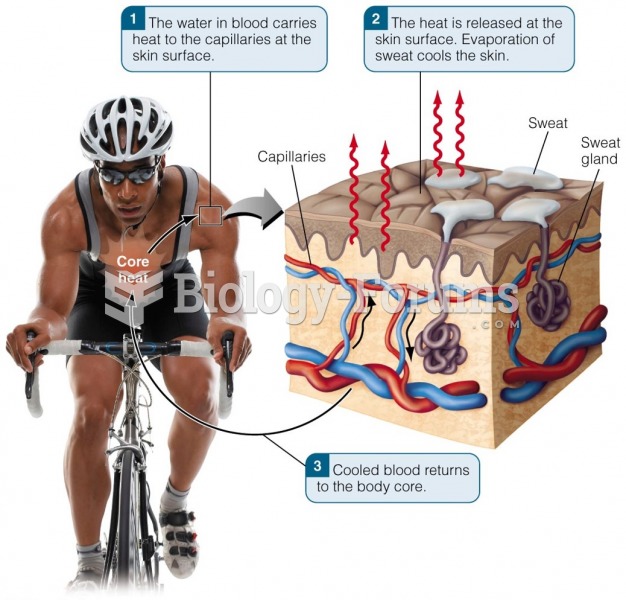
|
|
|
The toxic levels for lithium carbonate are close to the therapeutic levels. Signs of toxicity include fine hand tremor, polyuria, mild thirst, nausea, general discomfort, diarrhea, vomiting, drowsiness, muscular weakness, lack of coordination, ataxia, giddiness, tinnitus, and blurred vision.
There are immediate benefits of chiropractic adjustments that are visible via magnetic resonance imaging (MRI). It shows that spinal manipulation therapy is effective in decreasing pain and increasing the gaps between the vertebrae, reducing pressure that leads to pain.
The use of salicylates dates back 2,500 years to Hippocrates's recommendation of willow bark (from which a salicylate is derived) as an aid to the pains of childbirth. However, overdosage of salicylates can harm body fluids, electrolytes, the CNS, the GI tract, the ears, the lungs, the blood, the liver, and the kidneys and cause coma or death.
The immune system needs 9.5 hours of sleep in total darkness to recharge completely.
In 1835 it was discovered that a disease of silkworms known as muscardine could be transferred from one silkworm to another, and was caused by a fungus.