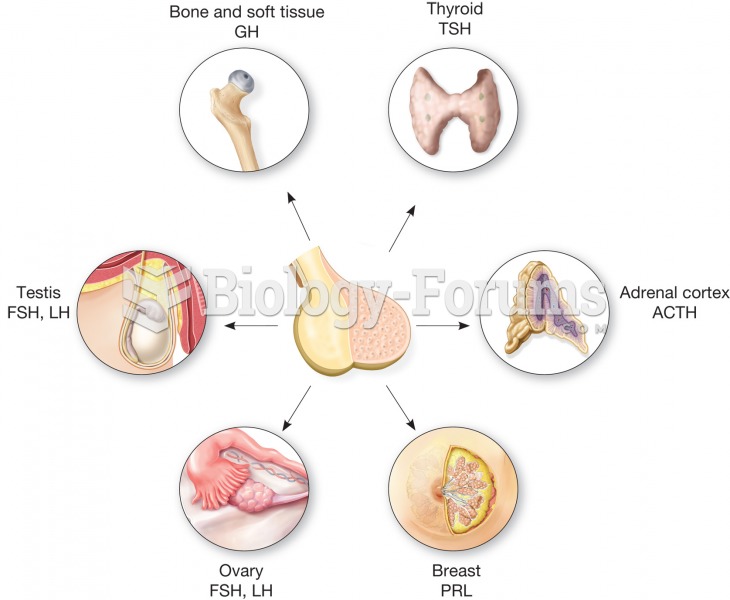
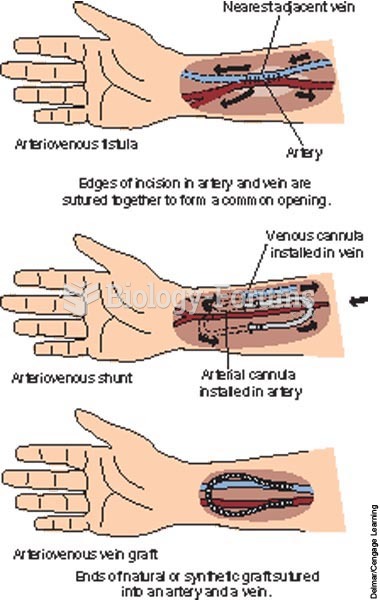
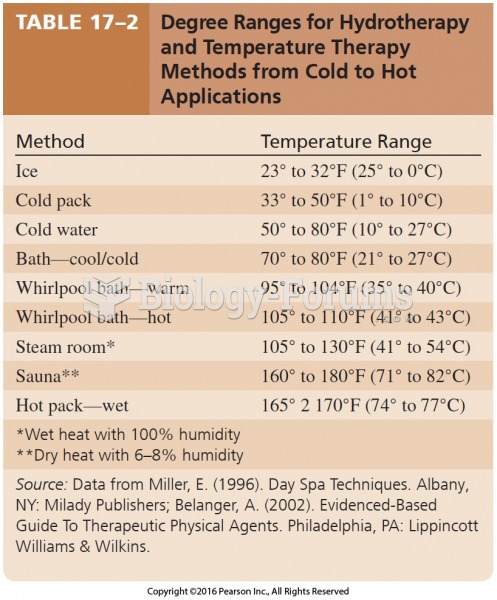
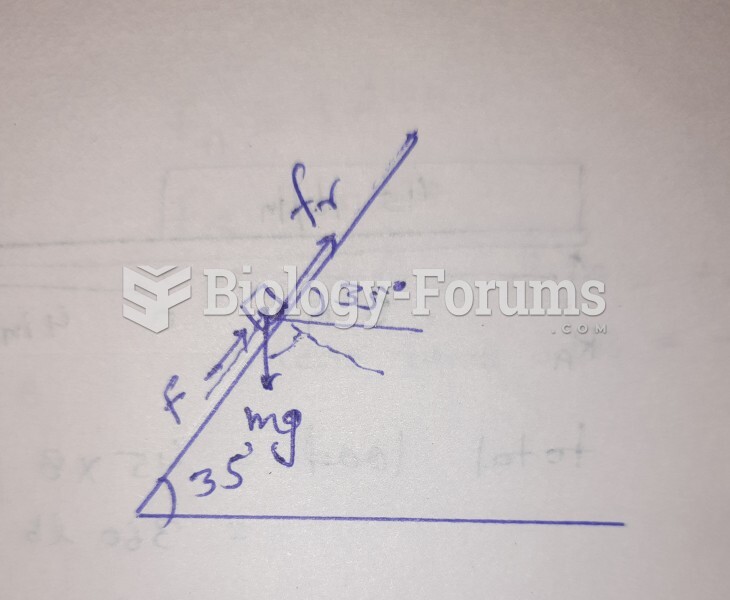
|
|
|
The U.S. Pharmacopeia Medication Errors Reporting Program states that approximately 50% of all medication errors involve insulin.
The top five reasons that children stay home from school are as follows: colds, stomach flu (gastroenteritis), ear infection (otitis media), pink eye (conjunctivitis), and sore throat.
About 3% of all pregnant women will give birth to twins, which is an increase in rate of nearly 60% since the early 1980s.
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
Elderly adults are living longer, and causes of death are shifting. At the same time, autopsy rates are at or near their lowest in history.