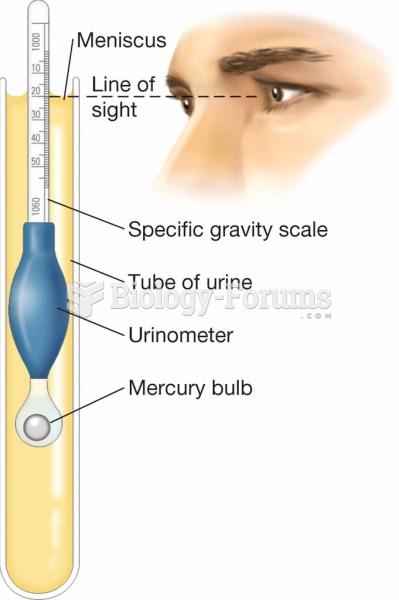
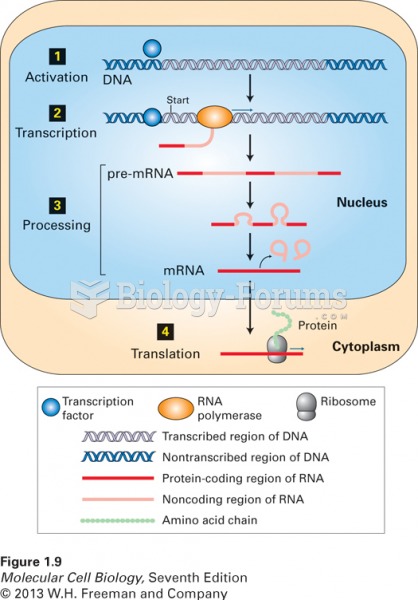
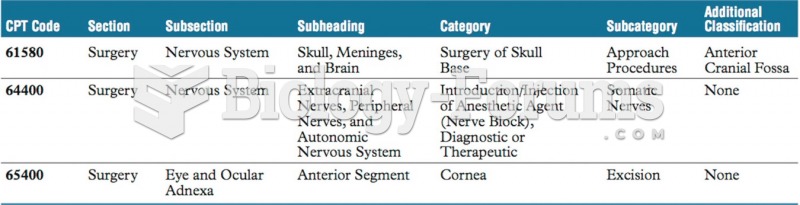
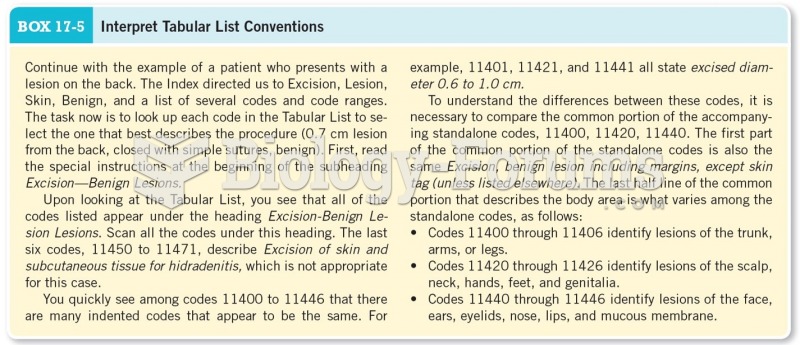
|
|
|
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
Pink eye is a term that refers to conjunctivitis, which is inflammation of the thin, clear membrane (conjunctiva) over the white part of the eye (sclera). It may be triggered by a virus, bacteria, or foreign body in the eye. Antibiotic eye drops alleviate bacterial conjunctivitis, and antihistamine allergy pills or eye drops help control allergic conjunctivitis symptoms.
Atropine, along with scopolamine and hyoscyamine, is found in the Datura stramonium plant, which gives hallucinogenic effects and is also known as locoweed.
An identified risk factor for osteoporosis is the intake of excessive amounts of vitamin A. Dietary intake of approximately double the recommended daily amount of vitamin A, by women, has been shown to reduce bone mineral density and increase the chances for hip fractures compared with women who consumed the recommended daily amount (or less) of vitamin A.
Russia has the highest death rate from cardiovascular disease followed by the Ukraine, Romania, Hungary, and Poland.